Checkra1n Jailbreak [Supports iOS 14.8 - iOS 12.3]

Checkra1n Jailbreak for iOS 14 to the latest iOS 14.8 is now available. Checkra1n Jailbreak has been released from iOS 12 up to iOS 14.8 jailbreak and available for macOS, Linux and Windows.
There is no online method or mobile based method to install Checkra1n yet. Also this jailbreak cannot be patched by a firmware update. The only limitation in Checkra1n is that it does not support the latest devices like iPhone 11, 11 Pro and 11 Pro Max and the latest iPhone 12 models. Unc0ver Jailbreak supports these latest devices but there is a limitation that it only supports upto iOS 14.3. Find Jailbreak Tools which support latest devices. If you have a iPhone 5S - iPhone X device, lets see how to jailbreak using Checkra1n.
So let's find out the best Checkra1n Jailbreaking process for you.
- Check your device Checkra1n compatibility
- Checkra1n jailbreak for Windows
- Checkra1n jailbreak for Mac
- Checkra1n jailbreak for Linux
- Online jailbreak solutions for un-compatible devices
Checkra1n Downloader & Compatibility Checker
Checkra1n Downloder is a Checkra1n Compatibility Checker Tool. You can simply check the compatibility of Checkra1n for your device using Checkra1n Downloader. Also you are able to find the best available Checkra1n Download for 100% Free or with $4.99 Premium Support
Tap the button below button to check the compatibility and download checkra1n using Checkra1n Downloader.
Checkra1n Downloader / Compatibility CheckerStep by step guide for checking Checkra1n Jailbreak Compatibility using Checkra1n Downloader
Step 1: Visit Checkra1n Downloader using your personal computer / iPhone.
Step 2: Select your device model and iOS / iPadOS version and click the check compatibility button.
Step 3: Then select your computer / PC's operating system (Windows, Linux or Mac). Then click on the given tools to download.
If your device is not compatible with checkra1n jailbreak it will show the available jailbreak alternatives for your device's OS version.
Step 4: Then provide your email in the given selection and go through the instructions they provided to get Checkra1n Tool / Premium User Guide.
Checkra1n Jailbreak for Windows users
Checkra1n Jailbreak is only available for Mac and Linux users for now. But the Checkra1n team says Checkra1n will support Windows, till then you can download checkra1n windows through another way mentioned, check it out.
The release note of the Checkra1n v0.12.2 says as follows.
"This beta is only available for macOS and Linux. Work is ongoing to support Windows, which will be added in a later release."
However there is a Checkra1n Alternative available for Windows users named Ra1nstorm.
See more about Ra1nstorm.
1. Ra1nstorm
Ra1nstorm Jailbreak is the Checkra1n Jailbreak tool for Windows and Linux. This is now available in computer method. This was a tool developed by @realra1nstorm. Ra1nstorm will work on iPads and iPods also other than iPhones.
Download Ra1nstorm for WindowsDownload Ra1nstorm for Linux
Special Note:
- Do not use Ubuntu from a USB flash drive since this will crash the system.
- There might be bugs as this is a beta verison yet. Fair warning!
- Windows users: use the "setup.exe" that prepares a Linux environment. Once Xubuntu is installed using setup.exe, you run "/host/ra1nstorm/ra1nstorm.run" in order to begin ra1nstorm setup
- Ubuntu and derivative distro users can just run "ra1nstorm.run" file using bash.
- You need to disable Secure Boot in your BIOS. It varies by motherboard and computer, but it is generally simple to do and the option is always labeled Secure Boot.
You may need to enable VT-d and here is the way to enable it.
- Enter the computer BIOS (probably F12 on boot)
- Navigate to an "Advanced" tab
- Select the "VT-d" or similar option
- Enable it
- Reboot
2. Ra1nUSB Jailbreak
Ra1nUSB is not a new jailbreak tool but a USB bootable version of Checkra1n Jailbreak. If you own a Mac OS, you can use checkra1n. If you are a windows user or a linux user, you may use Ra1nstorm helper or the newly introduced Ra1nUSB Jailbreak.
Before downloading Ra1nUSB, you may find the suitable image file for your PC. Please choose the one which is relevant to you from the below download buttons.
Ra1nUSB for IntelRa1nUSB for AMD
Before using Ra1nUSB
1. Make sure you download Ra1nUSB according to your PC (Intel / AMD)
2. Prepare an 8GB USB flash drive which can be formatted if necessary
3. Access to the BIOS settings of your computer, If you have any BIOS passwords set, make sure that you remember those.
Step by Step Guide to Install Ra1nUSB
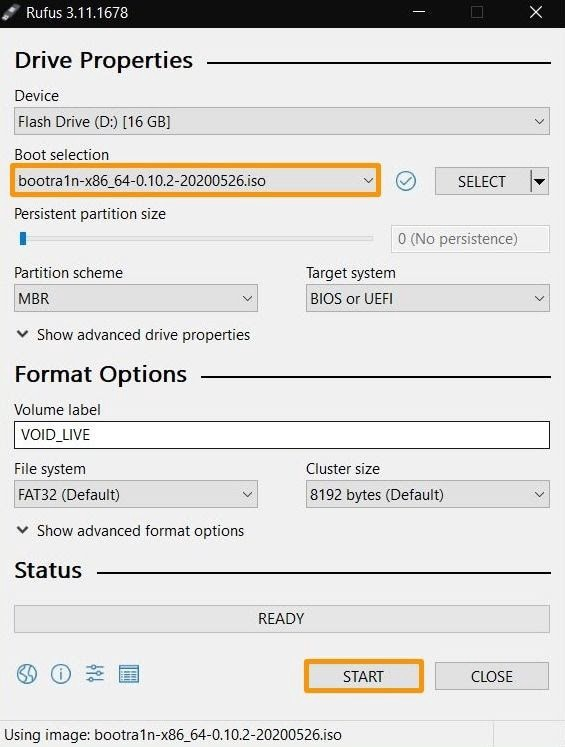
Step 1: Download Ra1nUSB according to your PC (Intel / AMD).
Step 2: Create a bootable USB using Rufus or any other creator like etcher. Make sure you select Ra1nUSB image during the create process
Step 3: This step changes BIOS settings of your computer and it is not recommended to continue to this process if you are not aware what you are doing,
Shut down your PC and boot into its BIOS by pressing the F10/F12 or DELETE button during the startup process. In the BIOS, go ahead and disable the following features:
- VT-D
- EL SerialPort
- Stack Network
- Fastboot
- Wake on LAN
After disabling the above features enable the Virtualization options in BIOS. Most of the systems come with Virtualization options enabled by default. If it is already enabled, just keep it as it is and do not change it. Save the settings by and exit.
Step 4: Plug the created Bootable USB and reboot your PC using the USB. Then select Boot macOS Install from Ra1nUSB option. This will boot into checkra1n installed Mac OSX.
*** If you get an error in this process, you may reboot the PC.
Step 5: If the system boots up properly, just go to the terminal by pressing Windows Key + T or using Utilities > Terminal
Step 6: Type “ra1nusb” command in the terminal and follow Checkra1n Jailbreak guide above.
Ra1nUSB Compatible Devices
As Ra1nUSB is nothing but preinstalled checkra1n in MacOSX, the compatible devices are between A5 - A11 and as mentioned above.
3. Webra1n
Webra1n is a web based interface to run Checkra1n Jailbreak on devices like Raspberry Pi. It supports all the versions which checkra1n supports and works only in MacOSX like the original Checkra1n Jailbreak. Then it enables the web interface to run and execute commands using Checkra1n.
Checkra1n Jailbreak for Mac users
Checkra1n Jailbreak for Mac users available for iOS 13.7 - iOS 12.3 Jailbreak (iPhone X and Below) and iOS 14.8 - iOS 14 Jailbreak (A11 and below). You can Download Checkra1n Jailbreak using Checkra1n Downloader.
Step by Step Guide of Checkra1n Jailbreak [Mac Method]
Here is the step by step guide to jailbreak your device using Checkra1n jailbreak. You should complete the following requirements before jailbreak using Checkra1n Jailbreak.
1. Your device should be compatible with Checkra1n Jailbreak. See which devices support Checkra1n Jailbreak ?
2. iPhone running on iOS 12.3 - iOS 14.8
3. You should have a Mac with the latest version of iTunes installed.
4. Latest Checkra1n Jailbreak App. Download Checkra1n from Checkra1n Downloader.
Now follow the below steps guide.
Step 1: Connect your iPhone / iPad to your computer using USB. Then open the Checkra1n jailbreak app.
Note: Give all permissions to the app. Disable FileVault if there is any problem occurs.
Step 2: Click the Start button and then click Next.
Step 3: Now put your iPhone / iPad into DFU mode. See how to put your device to DFU mode +

Step 4: Wait for the jailbreak process. Your device will restart after the process has completed. Now you can see the Checkra1n app on your device’s home screen.
Step 5: Run checkra1n app and install Cydia. After installing Cydia your device will restart and then you can see the Cydia icon on your device’s home screen.
Checkra1n Jailbreak for Linux users
Checkra1n Jailbreak supported Linux for iOS 14.8 - iOS 12.3. You can download Checkra1n for Linux using Checkra1n Downloader.
Step by Step Guide of Checkra1n Jailbreak [Linux Method]
Note: Download Checkra1n for Linux using Checkra1n Downloader according to your computer OS. There are CLI versions for x86_64, arm, arm64, and i486 architectures. Please check your system architecture and download the correct file.
Step 1: Open downloaded Checkra1n file and open terminal. Then type the following commands on the terminal.
- chmod +x (drag and drop the checkra1n folder).
- Sudo (drag and drop the checkra1n folder).
Step 2: if you have already set up a device password, it will ask the password. If not checkra1n Linux jailbreak will open your computer screen. Now you can click the start button and proceed to the jailbreak. (Same as Mac method).
Online jailbreak solutions for un-compatible devices
If your latest iOS 14.8 running iPhone / iPad not supported for the Checkra1n jailbreak tool, you can use online jailbreak solutions listed below to enjoy jailbreak tweaks, hacked game, apps and many more.
1 . Ataler

2. TaigOne

Checkra1n Supported iOS Versions
iOS 14.7.1, iOS 14.7, iOS 14.6, iOS 14.5.1, iOS 14.5, iOS 14.4.2, iOS 14.4.1, iOS 14.4, iOS 14.3, iOS 14.2.1, iOS 14.2, iOS 14.1, iOS 14.0.1, iOS 14, iOS 13.7, iOS 13.6.1, iOS 13.6, iOS 13.5.1, iOS 13.5, iOS 13.4.1, iOS 13.4, iOS 13.3.1, iOS 13.3, iOS 13.2.3, iOS 13.2.2, iOS 13.2, iOS 13.1.3, iOS 13.1.2, iOS 13.1.1, iOS 13.1, iOS 13, iOS 12.5.4, iOS 12.5.3, iOS 12.5.2, iOS 12.5.1, iOS 12.5, iOS 12.4.9, iOS 12.4.8, iOS 12.4.7, iOS 12.4.6, iOS 12.4.5, iOS 12.4.4, iOS 12.4.3, iOS 12.4.2, iOS 12.4.1, iOS 12.4, iOS 12.3.2, iOS 12.3.1, iOS 12.3, iOS 12.2, iOS 12.1.4, iOS 12.1.3, iOS 12.1.2, iOS 12.1.1, iOS 12.1, iOS 12.0.1, iOS 12
Checkra1n Supported Devices
iPhone 5S, iPhone 6, iPhone 6 Plus, iPhone 6S, iPhone 6S Plus, iPhone SE (1st), iPhone 7, iPhone 7 Plus, iPhone 8, iPhone 8 Plus, iPhone X, iPad Mini 2, iPad Mini 3, iPad Mini 4, iPad 5th, iPad 6th, iPad 7th, iPad Mini 4, iPad Air, iPad Air 2, iPad Pro 1st, iPad Pro 2nd.
Please note that Checkra1n only supports iOS 12 - iOS 14.8 for iPhone 5S - iPhone X devices. The latest iOS 15 does not compatible with Checkra1n yet. You can find checkra1n compatibility with your device and iOS version clearly with Checkra1n Downloader
Advantages of Checkra1n Jailbreak
Running Android on iOS
It is possible to run the Android Operating System on the iPhone. For now iPhone 7 and 7 plus is possible to run the Android OS natively. Other devices will be supported later.
Cydia but No Zebra
As Checkra1n official page published checkra1n will get the other package manager access with the next release but only supports Cydia with the first beta release.
Why Checkra1n?
Cannot be patched by any iOS update. Once jailbroken it will last until user unjailbreak it. Further latest version and coming versions also will be compatible with the jailbreak.
Latestly released iOS 14.8 also successfully jailbroken by the Checkra1n jailbreak. iOS 15 is not yet supported the Checkra1n. However, the most recent jailbreak tool introduced for iOS 15.4.1 - iOS 15 jailbreak in the Palera1n jailbreak tool which is semi-untethered and only available in the developer version for the time being.
Also, until iOS 15 Checkra1n jailbreak supports, we have a few alternative methods for iOS 15 jailbreak.
